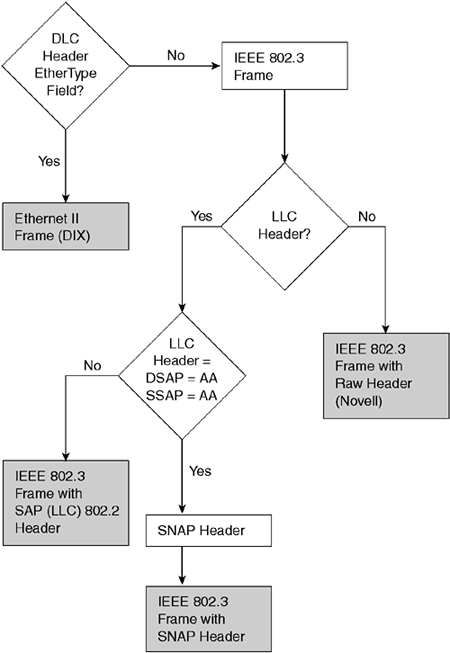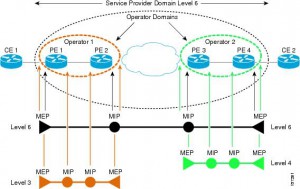
ME Maintenance Entity
MEG ME Group
MEL MEG Level
MEP MEG End Point
MIP MEG Intermediate Point
Eight MEG Levels are available to accommodate different network deployment scenarios:
• Customer role is assigned three MEG Levels: 7, 6, and 5.
• Provider role is assigned two MEG Levels: 4 and 3.
• Operator role is assigned three MEG Levels: 2, 1, and 0.
Transmission periods:
• 3.33 ms: Default transmission period for protection switching application (transmission rate of 300 frames/second).
• 10 ms: (Transmission rate is 100 frames/second).
• 100 ms: Default transmission period for performance monitoring application (transmission rate of 10 frames/second).
• 1 s: Default transmission period for fault management application (transmission rate of 1 frame/second).
• 10 s: (Transmission rate of 6 frames/minute).
• 1 min: (Transmission rate of 1 frame/minute).
• 10 min: (Transmission rate of 6 frames/hour).
Fault management
CCM Continuity Check Message
If no CCM frames from a peer MEP are received within the interval equal to 3.5 times the
receiving MEP’s CCM transmission period, loss of continuity with peer MEP is detected.
—
Ethernet Loopback function (ETH-LB) is used to verify connectivity of a MEP with a MIP or peer
MEP(s).
LBM LoopBack Message
LBR LoopBack Reply
LBR frame within 5 seconds.
Transaction ID from the same MEP may be repeated within one minute.
Unicast ETH-LB:
• To verify bidirectional connectivity of a MEP with a MIP or a peer MEP.
• To perform a bidirectional in-service or out-of-service diagnostics test between a pair of
peer MEPs. This includes verifying bandwidth throughput, detecting bit errors, etc.
The MIP or peer MEP is identified by its MAC address. This MAC address is encoded in the DA of the Unicast request frame. Transmitted only by MEP on the on-demand basis.
Multicast ETH-LB:
Multicast ETH-LB function is used to verify bidirectional connectivity of a MEP with its peer
MEPs. When Multicast-LB is invoked on a MEP, a Multicast frame with ETH-LB request information is sent from a MEP to other peer MEPs in the same MEG. A MIP is transparent to the Multicast frames with ETH-LB request information.
—
Ethernet Link Trace function (ETH-LT)
• Adjacent Relation Retrieval – ETH-LT function can be used to retrieve adjacency
relationship between a MEP and a remote MEP or MIP. The result of running ETH-LT
function is a sequence of MIPs from the source MEP until the target MIP or MEP. Each
MIP and/or MEP is identified by its MAC address.
• Fault Localization – ETH-LT function can be used for fault localization. When a fault (e.g.,
a link and/or a device failure) or a forwarding plane loop occurs, the sequence of MIPs
and/or MEP will likely be different from the expected one. Difference in the sequences
provides information about the fault location.
LTM Link Trace Message
LTR Link Trace Reply
LTR frames within 5 seconds.
Transaction ID from the same MEP may be repeated within one minute.
If the TTL field value is 0, the LTM frame is discarded.
Only LTM frames with the same MEG Level
As each network element, containing the MIPs or MEP, needs to be aware of the TargetMAC
address in the received LTM frame and associates it to a single egress port, in order for the MIP or MEP to reply, a Unicast ETH-LB to the TargetMAC address could be performed by a MEP before transmitting the LTM frame.
—
Ethernet Alarm Indication Signal function (ETH-AIS)
Suppress alarms following detection of defect conditions at the server (sub) layer. ETH-AIS is not expected to be applied in the STP environments.
—
Ethernet Remote Defect Indication function (ETH-RDI) can be used by a MEP to communicate to
its peer MEPs that a defect condition has been encountered.
—
Ethernet Locked Signal function (ETH-LCK) is used to communicate the administrative locking of a server (sub) layer MEP and consequential interruption of data traffic forwarding towards the MEP expecting this traffic. It allows a MEP receiving frames with ETH-LCK information to differentiate between a defect condition and an administrative locking action at the server (sub) layer MEP. An example of an application that would require administrative locking of a MEP is the out-of-service ETH-Test.
—
Ethernet Test Signal function (ETH-Test) is used to perform one-way on-demand in-service or outof-service diagnostics tests. This includes verifying bandwidth throughput, frame loss, bit
errors, etc.
Different Sequence Number must be used for every TST frame, no Sequence Number from the
same MEP may be repeated within one minute.
—
Ethernet Automatic Protection Switching function (ETH-APS) is used to control protection
switching operations to enhance reliability.
—
Ethernet Maintenance Communication Channel function (ETH-MCC) provides a maintenance
communication channel between a pair of MEPs. ETH-MCC can be used to perform remote
management.
A remote MEP, upon receiving a frame with ETH-MCC information and with a correct MEG
Level, passes the ETH-MCC information to the management agent which may additionally respond.
—
Ethernet Experimental OAM (ETH-EXP) is used for the experimental OAM functionality which can be used within an administrative domain on a temporary basis. Interoperability of the experimental OAM functionality is not expected across different administrative domains.
—
Ethernet Vendor Specific OAM (ETH-VSP) is used for vendor-specific OAM functionality which may be used by a vendor across its equipment. Interoperability of vendor-specific OAM functionality is not expected across different vendors’ equipment.
Performance monitoring
Frame Loss Measurement (ETH-LM)
—
Frame Delay Measurement (ETH-DM)
—
Throughput measurement